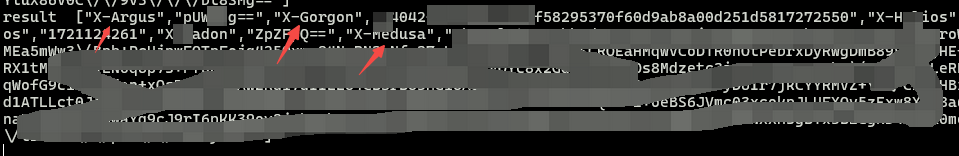
hook hashMap put 函数
1 | function hookMap(){ |
结果如下
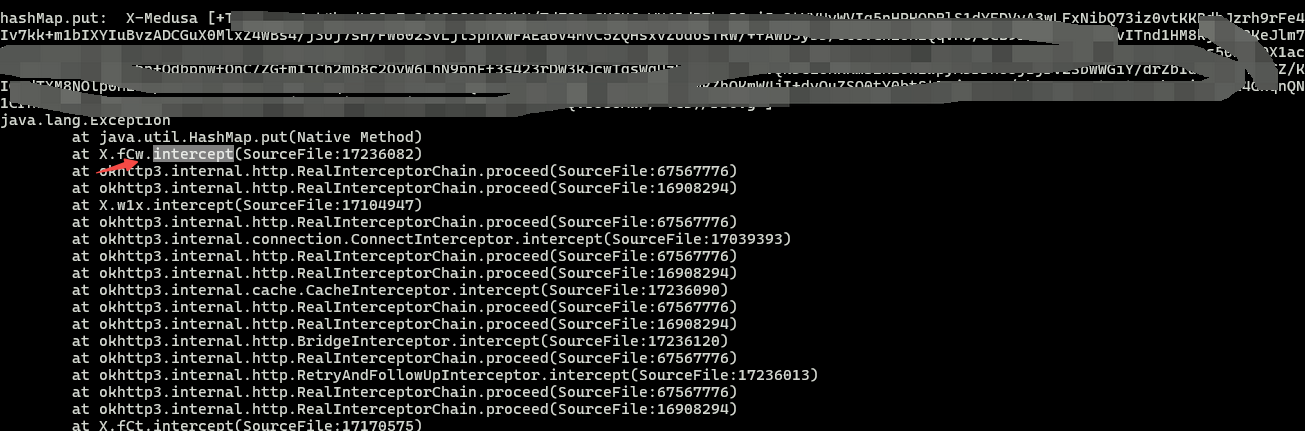
hook fCw试试, 看看在调用该函数的时候, 六神是否已经生成
hook 代码如下
1 | function hook_intercept(){ |
hook 结果如下
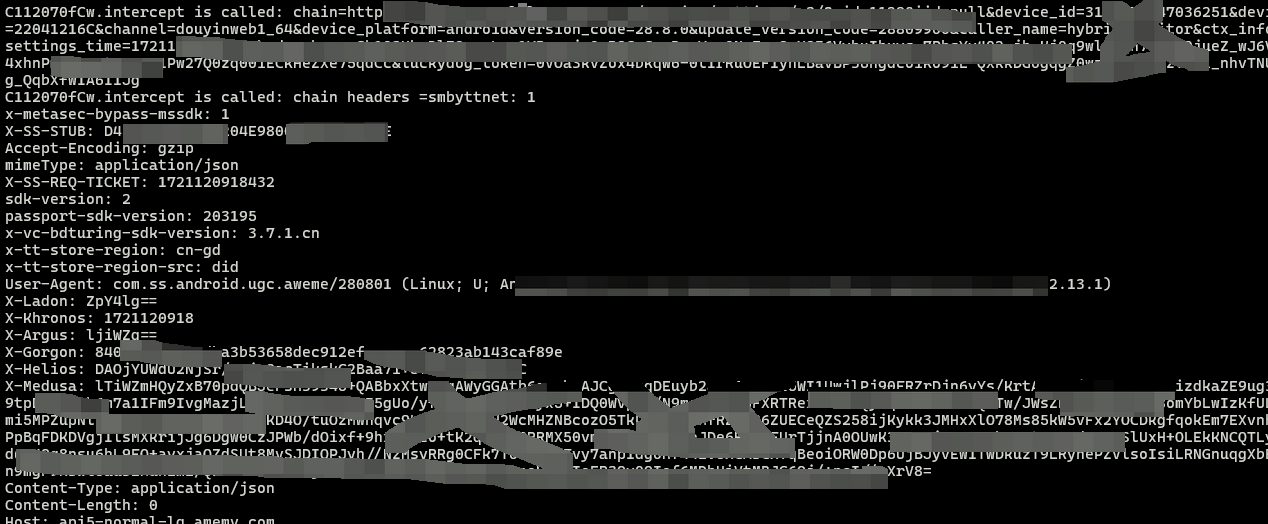
可以看到此处六神已经拿到了, 继续往上游函数摸索.
hook fct函数试试, hookfct函数发现headers 中没有 six
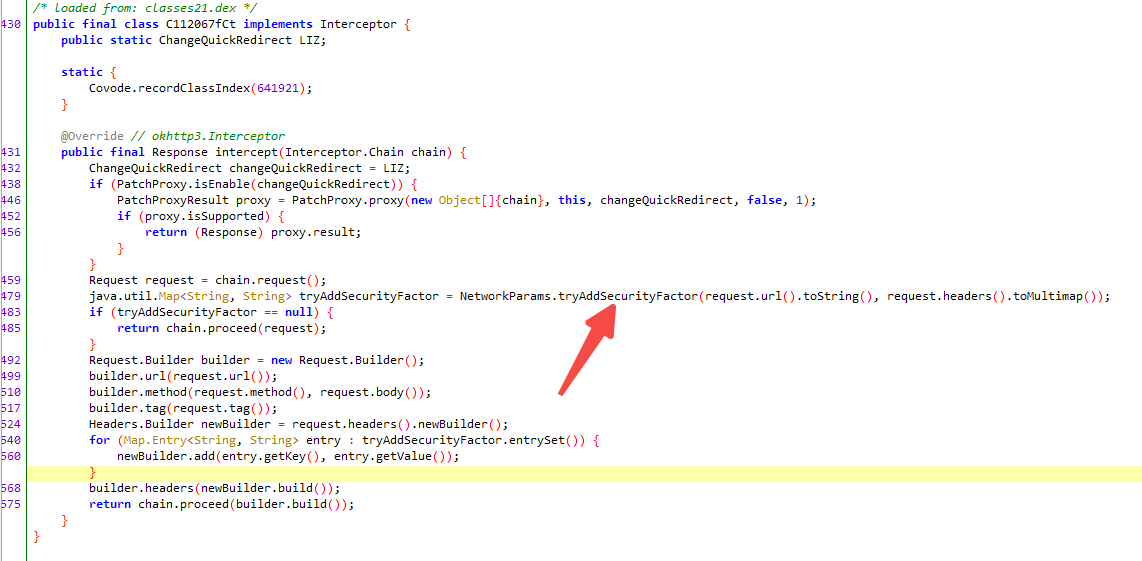
jadx打开看看
看看response fct函数以后, headers有没有增加six 字段
hook脚本如下
1 | function hook_intercept(){ |
结果如下
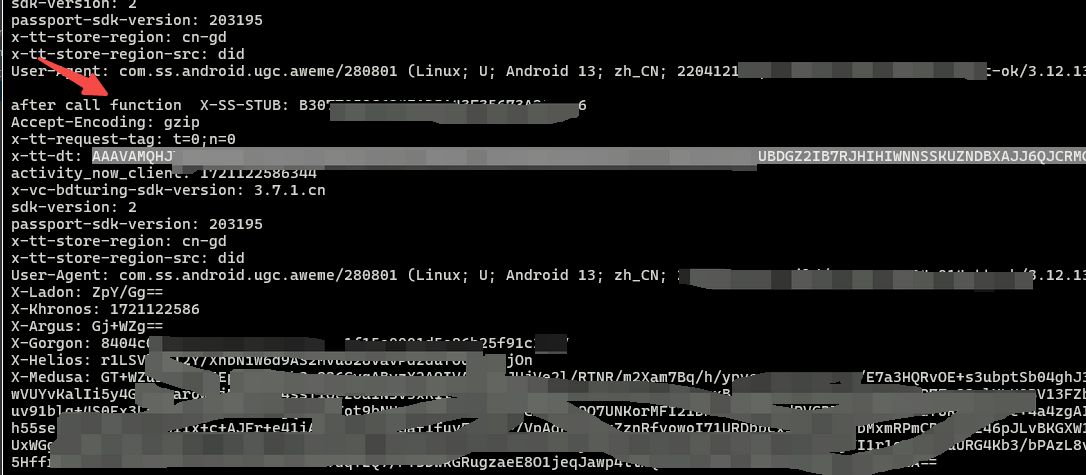
可以看到 经过 fCt 以后,six就出来了. 重点看看 fCt, tryAddSecurityFactor 很可疑, hook 看看, 要注意Map强转HashMap, 否则打印出来的就是 Obejct
1 | let NetworkParams = Java.use("com.bytedance.frameworks.baselib.network.http.NetworkParams"); |
hook 结果如下, 可以看到 six已经生成了
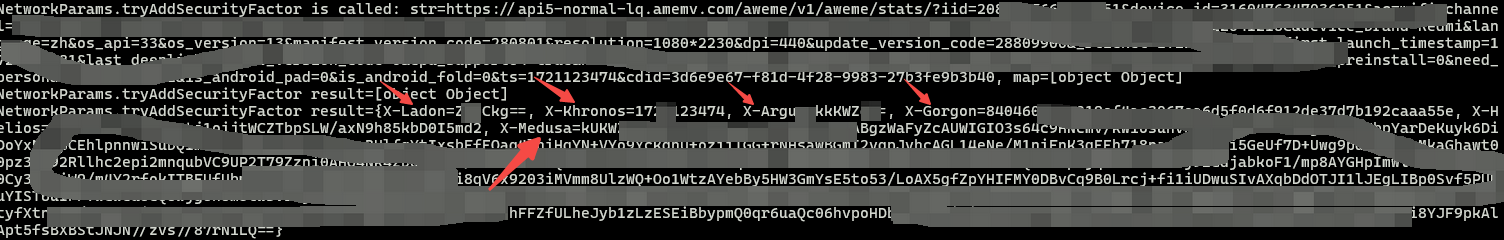
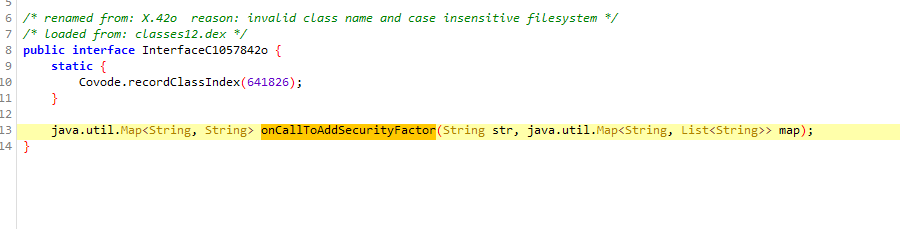
jadx继续看看 发现调用了 onCallToAddSecurityFactor, 进去看看实现, 发现是个接口
查看交叉引用看看
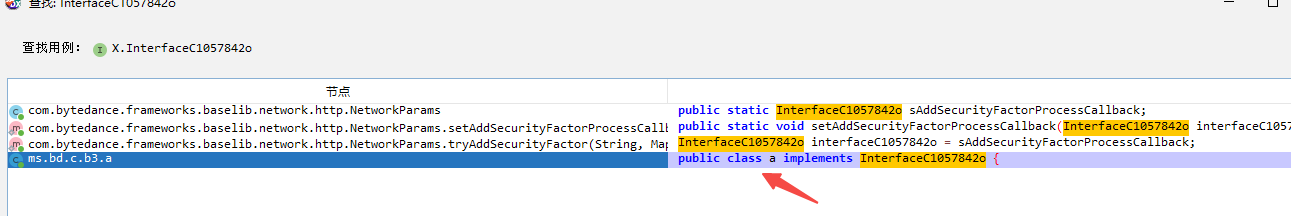
进入以后 发现调用了 l.a, hook 试试看
1 | Java.perform(function (){ |
结果如下