我们自己写了一个app, 现在对这个app进行trace
先看看so名
1 | cat /proc/$(pidof com.zj.my_md5 )/maps | grep checkout |
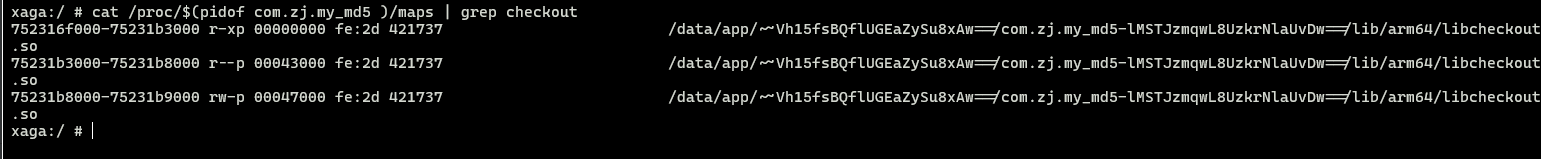
这是一个 64位的so. 名为 libcheckout.so
ida 打开看看目标so
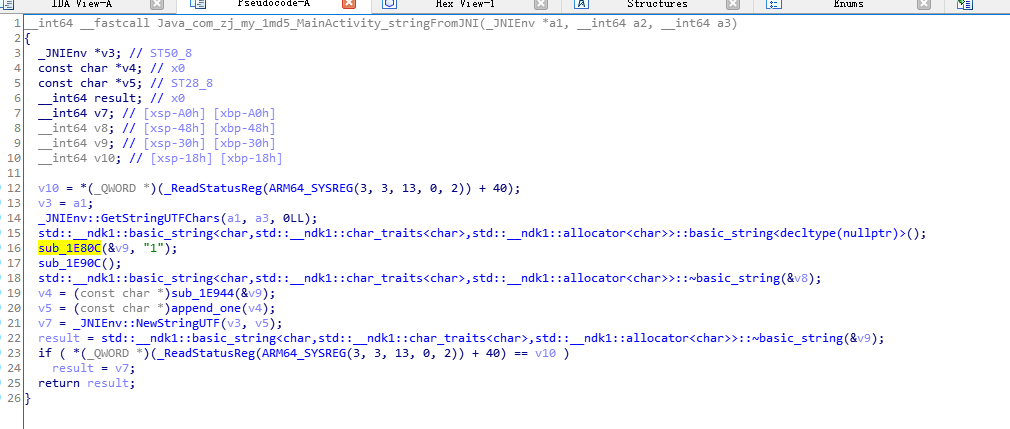
现在就使用 stalker 对这个函数进行trace
1 | function hook_native_stalker(){ |
遇到bl指令 就打印调用地址.
结果如下
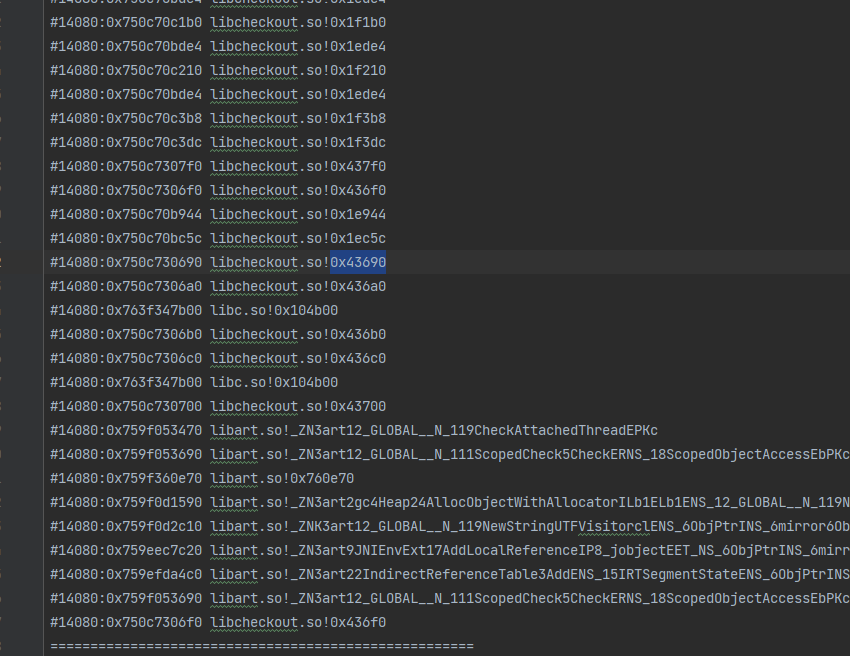
可以看到 0x43690 这个函数被调用。
ida看一下这个地址 正是关键函数.
使用frida stalker trace 一下某视频看看
1 |
|
每次执行bl指令时, 就打印当前pc, 并且尝试打印 cstring, x0
trace 结果如下
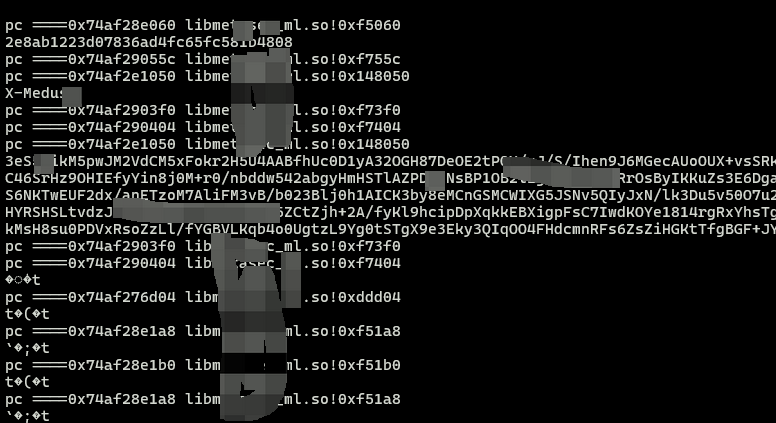
可以看到 核心算法结果已经出来了, 剩下得就是分析了.