抓包
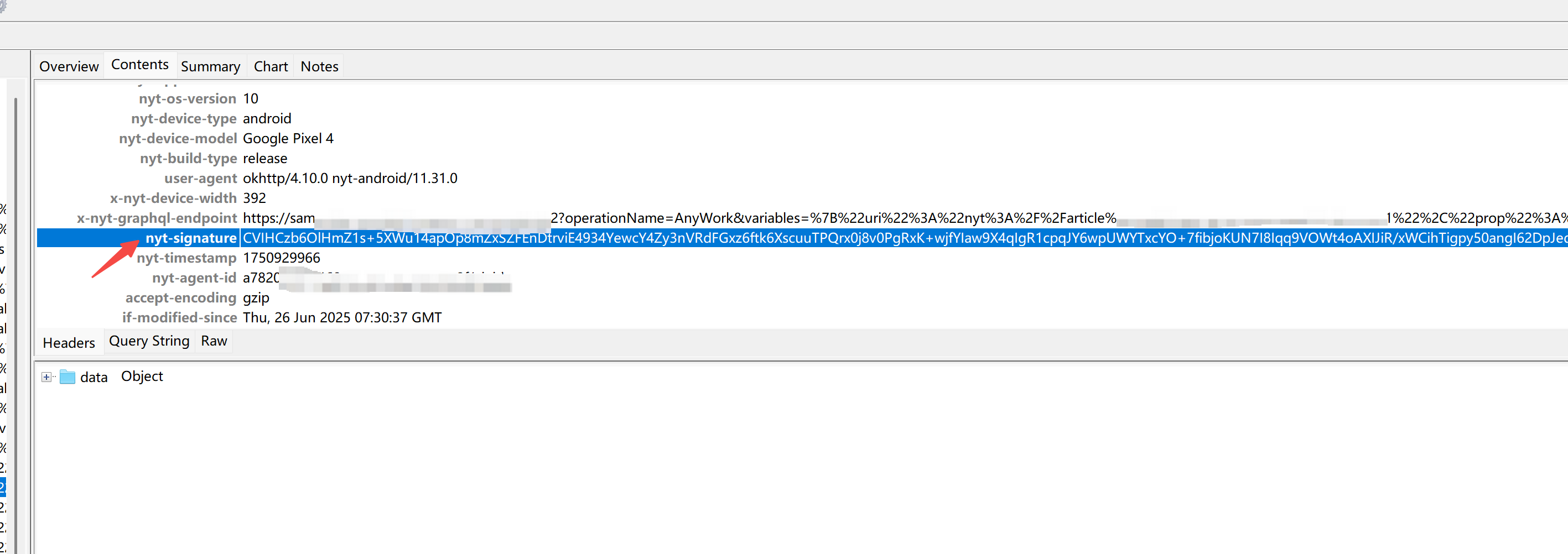
利用 charles 的 compose 功能 修改一个字符, 发现 403. 但是可以repeat, 但几分钟后 repeat 照样 403, 说明后台校验时间
jadx 全局搜索
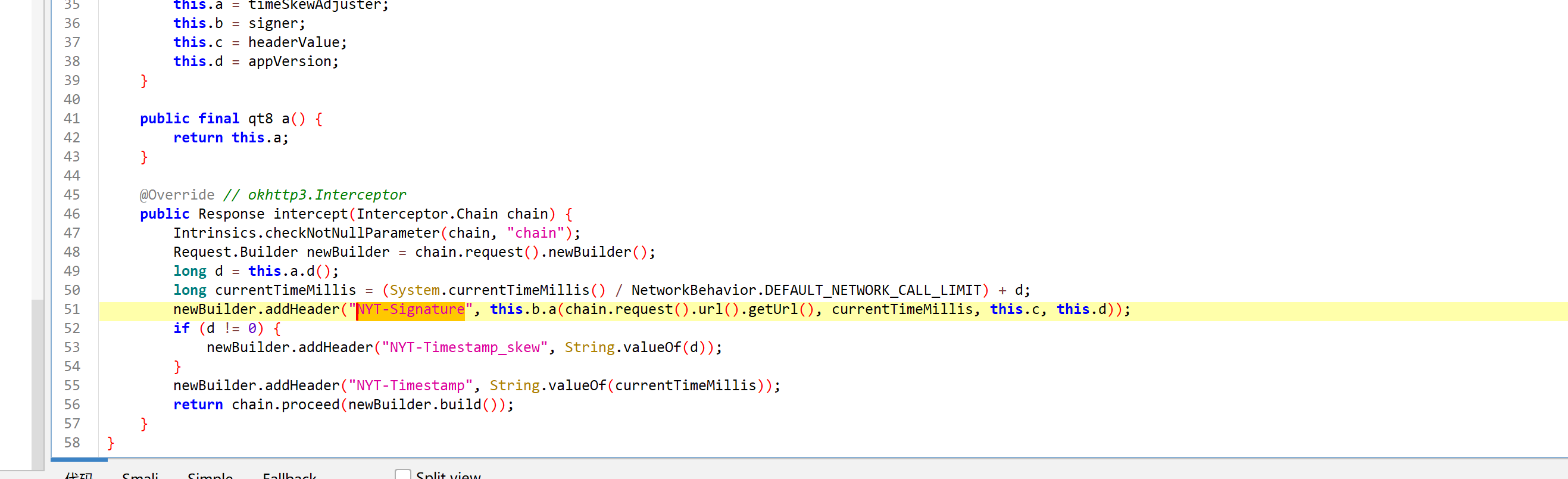
进入 this.b.a 看看
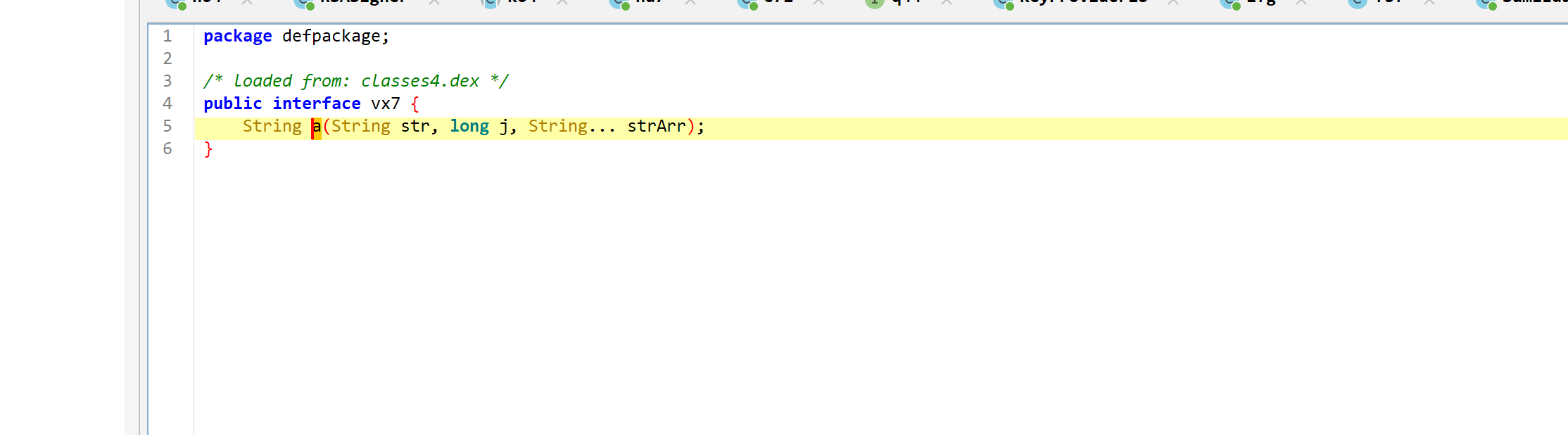
是个接口, 查看交叉引用.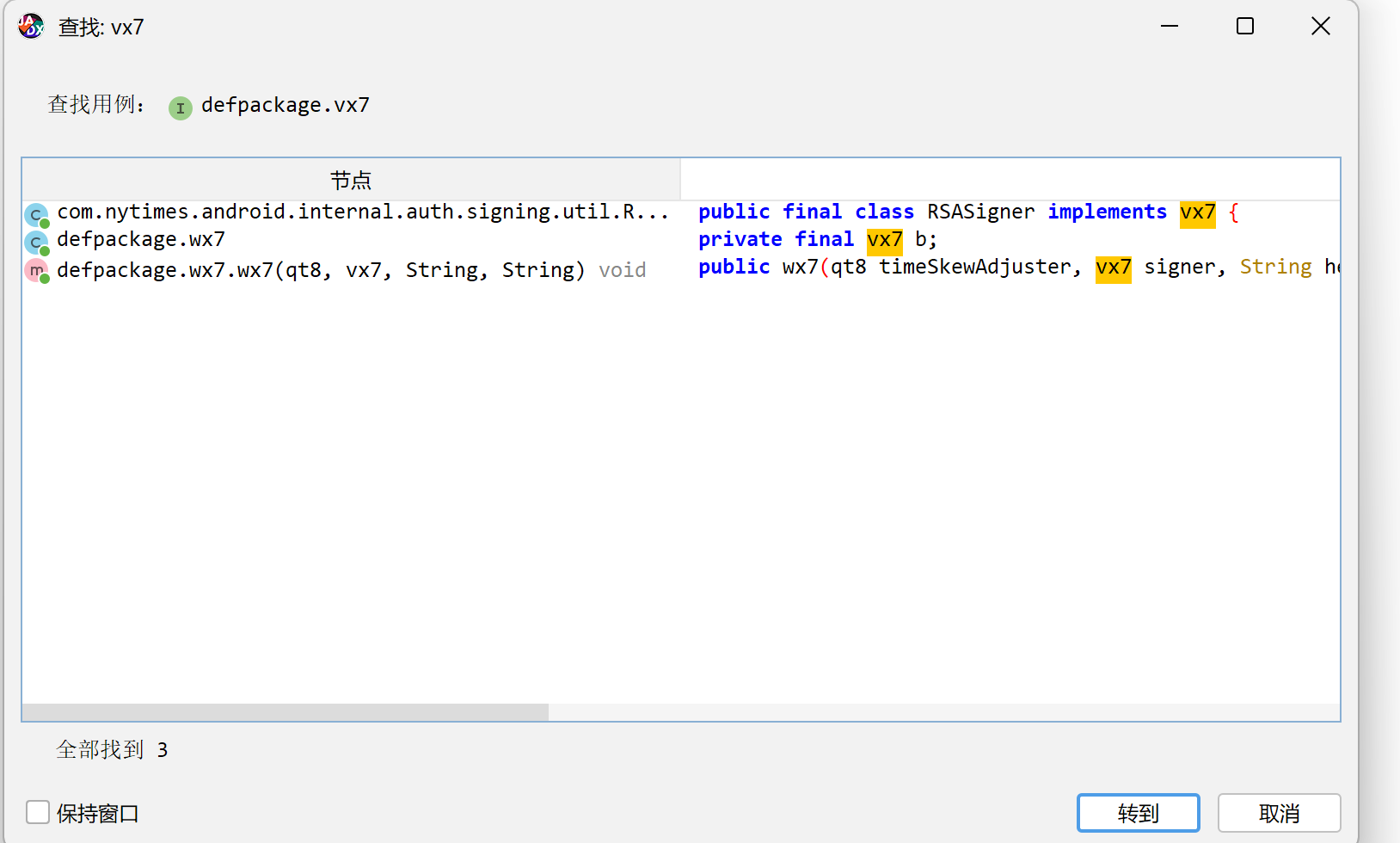
第一个很可疑, 我们进入看看
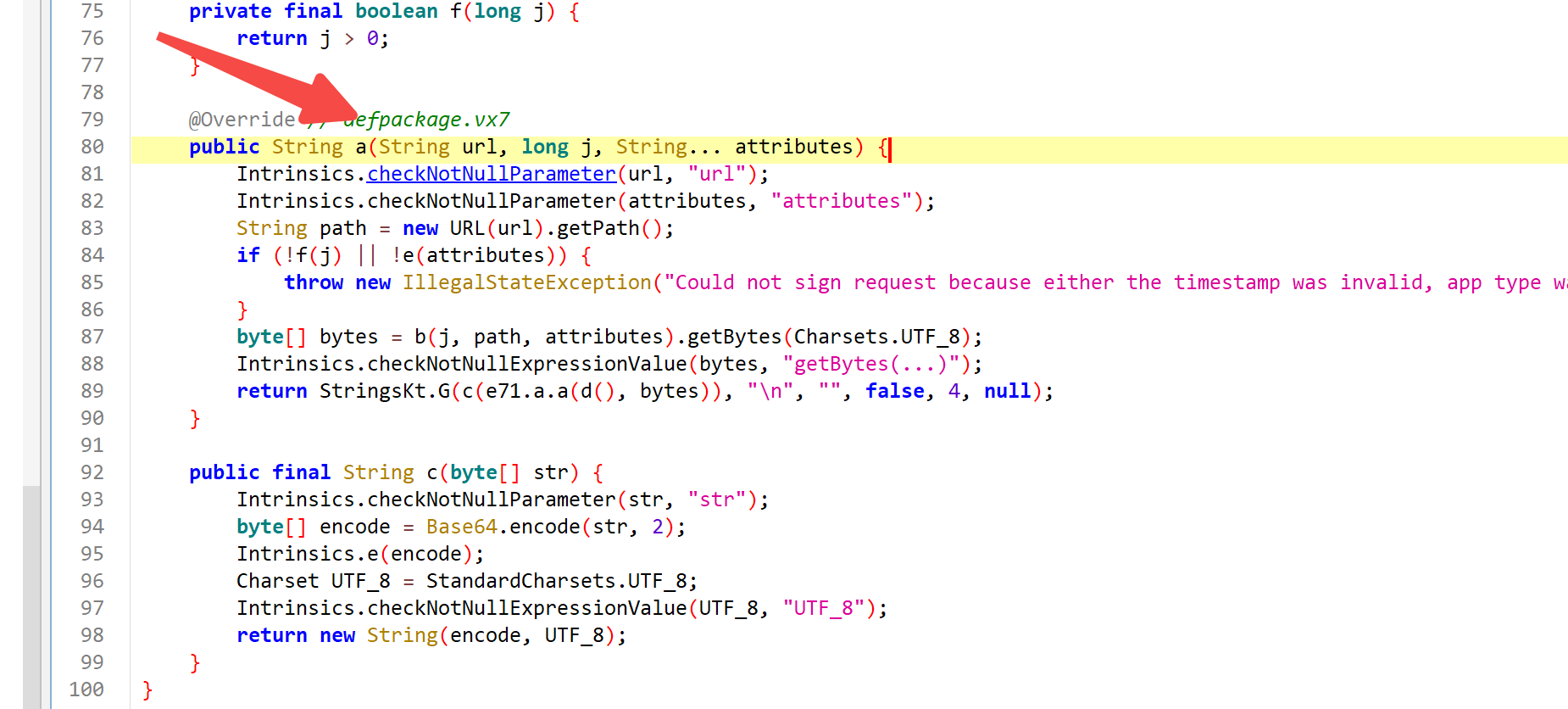
可以看到, 这个方法就是具体实现.
简单分析了一下, 其中 bytes 就是 时间 + url 路径 + app_type + version
关键函数是 e71.a.a, 我们进入这个函数看看.
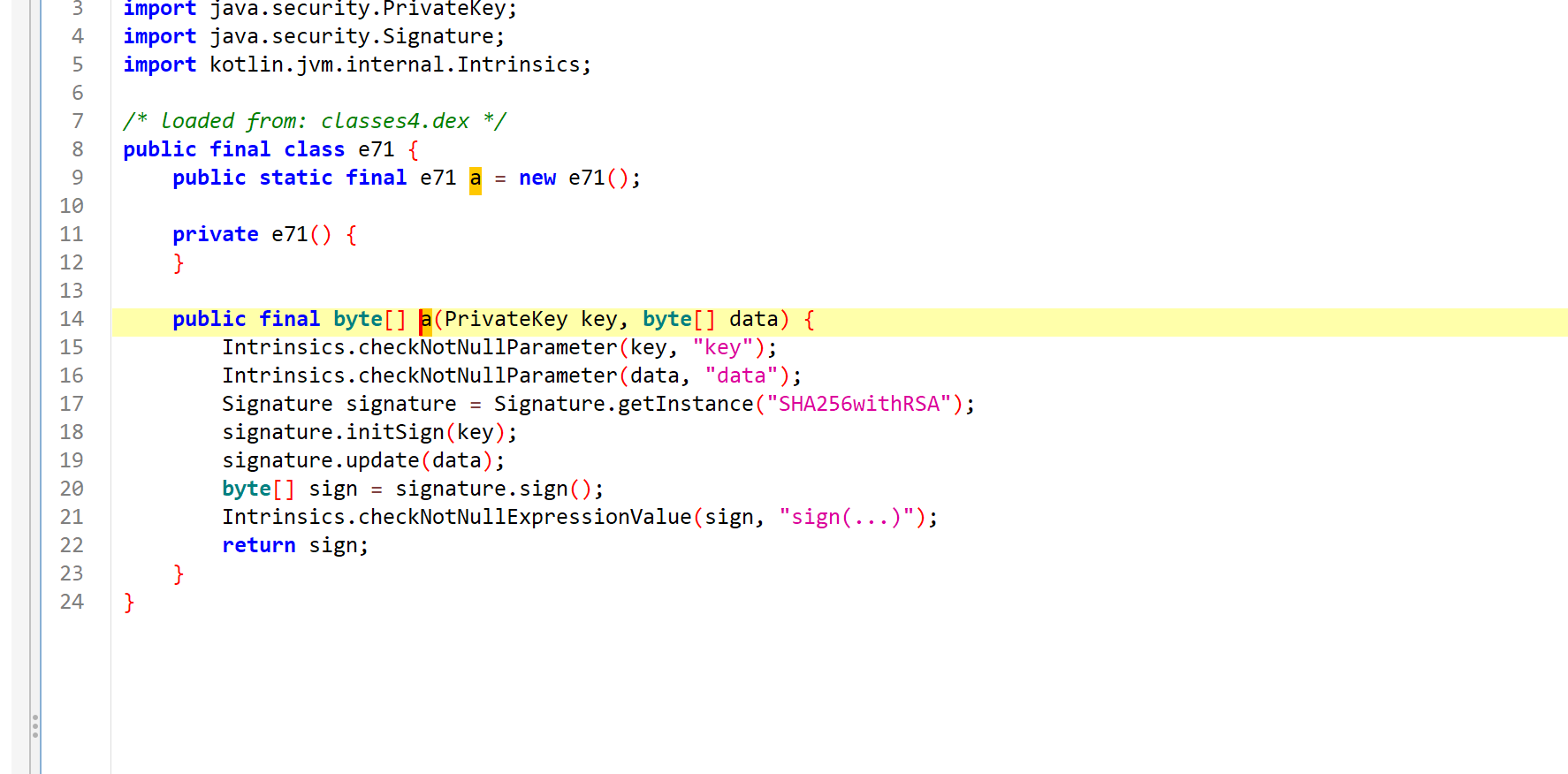
frida hook 看看
1 | function getJavaClassName(obj) { |
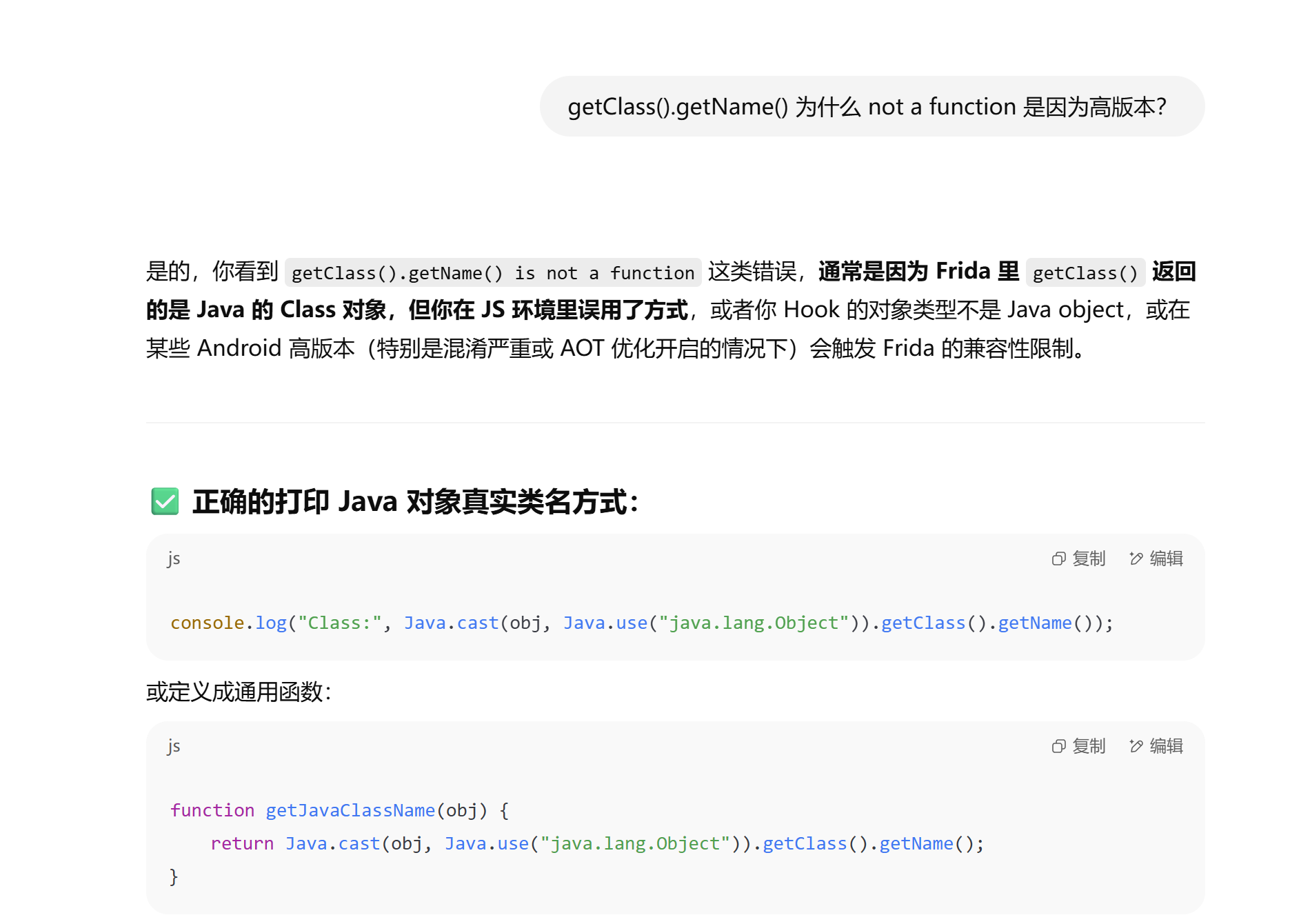
注意这里有两个坑, 一个是如何打印 privatekey 的问题, 另外一个是查看类型的问题, 总是 not a function, 我记得之前frida 还可以用
obj.getClass().getName() 来查看一个对象的类型的, 但是这个样本就是 not a function, 然后我降frida-server版本, 从 frida-server 16.6.6,
降为 frida-server 14.2.18, 还是 not a function, 我问了下chatgpt 和 deepseek 是这么解答的
我们再次打印 privatekey 的类型
PrivateKey class: com.android.org.bouncycastle.jcajce.provider.asymmetric.rsa.BCRSAPrivateCrtKey
然后交给chatgpt 问gpt 这个类型要怎么打印私钥.
结合 gpt 给出的答案, 我们整合一下代码, 最终的代码如下
1 | function getJavaClassName(obj) { |
我们再次 frida hook 一下,结果如下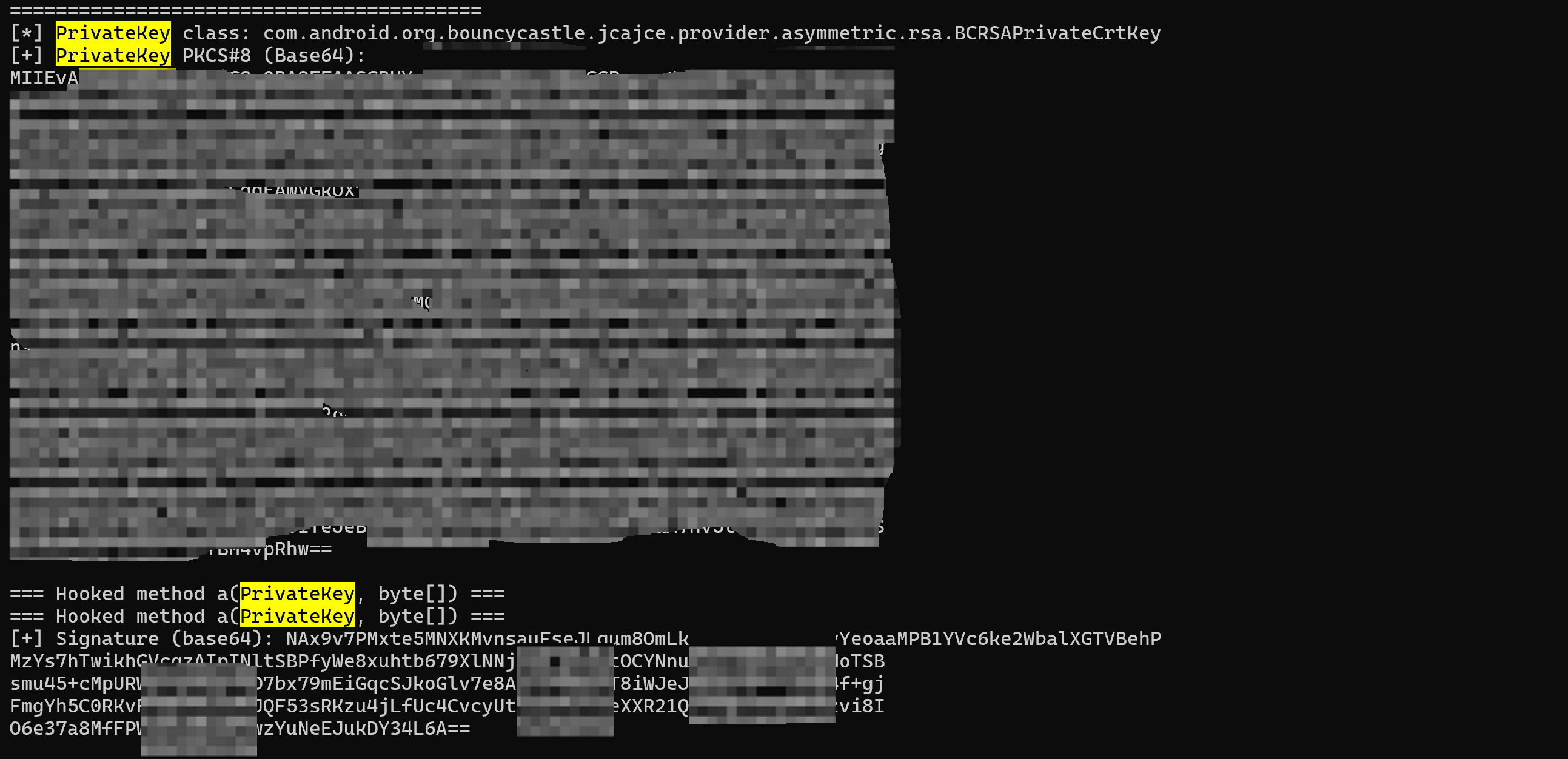
可以看到 私钥已经出来了, 剩下的就是如何 使用私钥进行 rsa sha256签名了, 下面给出 Java 代码
1 | import java.security.KeyFactory; |
然后运行 结果如下
然后用 java 生成的结果, 替换 charles 中的请求的加密参数. 发现可以成功获取到数据, 到此基本就成功了.
如何用 python 还原一份呢, 下面给出代码. 已下代码经过验证, 可成功通过校验.
1 | import base64 |
python 需要安装 cryptography
1 | python3 -m pip install cryptography -i https://pypi.tuna.tsinghua.edu.cn/simple |
通过私钥 进行签名, 使用的是 SHA256withRSA
改为 python 后,同样也可以生成加密结果 并且可以通过校验.
总结
- 遇到的核心问题, getClass().getName() 会报错 not a function, 可能是由于android 高版本的优化问题. 并不是 frida-server 和 frida 以及 frida-tools 的问题.
- privateKey 如何打印的问题, 上面已经给出答案. 还有些是通过 keyStore 这种, 这种导出就很麻烦.
- python3.8 安装 frida 14.2.18 会遇到 frida-14.2.18-py3.8-linux-x86_64.egg 问题, 直接下载 放到指定位置就好.
- 关于 RSA private, 或者 public key 也可以考虑 hook base64 的 decode 方法, 一般公钥要base64 解码后然后加载字节数据.
收获
在分析这个样本的过程中, 想借助一些文章, 发现了一些站点, 貌似可以低成本下载文档。
1 | http://toolman.dedyn.io:9192/#/main/csdnPaper |
充值了一块钱, 结果是个垃圾文章, 骗加公众号的, 无语子.
另外记录一下本人使用的 frida稳定的版本
1 | pip install frida==14.2.18 |